MERLIN LEGEND Communications System Release 6.1
Network Reference
555-661-150
Issue 1
August 1998
Call-Handling Scenarios
Page 2-16Network Configuration Scenarios
2
■ Remote access planning for private network usage by people who are
calling in either from outside the private network or from an extension that
is non-local to their home system
■ PRI dial-plan routed and DID calling across the private network
■ UDP routing for centralized VMS/AA
■ Considerations for PassageWay Telephony Service clients using the
system’s Computer Telephony Integration (CTI) link feature
The scenarios in this section do not show all of the types of equipment, such as
fax machines and single-line telephones, that may be included in systems. They
only include the types of equipment that are relevant to the examples. You can
use the same types of extension equipment in a networked system that you use in
a non-networked system.
To better understand your current system, review Scenario 1 if your private
network includes
any
tandem PRI trunks; review Scenario 2 if your system
includes
any
tandem tie trunks. Then review the remaining scenario that is most
like your own. When you are planning private network changes, review one or
more of the scenarios that involve system components and facilities for which you
are planning. Even though your own private network may not be represented here
exactly as it exists, information in a scenario that describes a similar configuration,
application, or facilities can be helpful to you.
If you are planning for a private network using Release 6.0, disregard the
information about centralized VMS/AA.
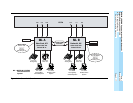
Scenario 1: Two Systems, Tandem PRI Facilities 2
In this scenario, two MERLIN LEGEND Communications Systems are connected
in a series configuration via tandem PRI trunks, which provide the best support for
features, call-handling displays, centralized VMS/AA, and performance across
private networks.
In this private network, the two system managers work closely together and
maintain copies of system forms for both systems. If changes must be made, they
first discuss them and assess their impact on the private network.