General configuration steps Example FortiGate Voice branch office configuration
FortiGate Voice Version 4.0 MR1 Administration Guide
18 01-410-112851-20100601
http://docs.fortinet.com/ • Feedback
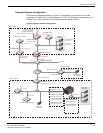
Figure 3: Example Branch Office network configuration
This section describes:
• General configuration steps
• Connecting the FortiGate Voice unit
• Configuring basic FortiGate Voice network and UTM settings
• Configuring network settings for the devices on the Internal network
• Configuring the FortiGate Voice PSTN and PBX settings
• Configuring the FortiFones on the internal network
• Adding extensions and configuring FortiFones for users behind a NAT device
General configuration steps
1 Connect the FortiGate Voice unit to the Internet, the internal network and the PSTN.
2 Configure FortiGate Voice unit network and UTM settings.
The network configuration includes enabling the SIP Traffic option on the internal and
wan1 interfaces. You must enable SIP traffic on these interfaces to accept and process
SIP calls. No other special network configuration, firewall policies, or routing is required
for the FortiGate Voice to accept and process SIP calls.
This example also describes how to configure the FortiGate Voice as a DHCP server
and DNS server for the branch office internal network. As a DHCP server the FortiGate
Voice can supply network configuration settings for the PCs and FortiFones on the
internal network.
3 Configure network settings for the PCs on the Internal network.
4 Configuring the FortiGate Voice PSTN and PBX settings.
Branch Office
Internal network
PCs with SIP soft phones
and FortiFones
Subnet: 172.20.120.0
Extension Range 6000 - 6999
PC
PC
PC
FortiFone
FortiFone
FortiFone
behind a NAT
device
NAT device
WAN WAN
fxo1
Head Office
IP: 192.168.30.10
Extention Range
2000 - 2999
VoIP Provider
IP: 192.168.20.10
Remote Users
with FortiFones or
SIP soft phones
Extension range
6000 - 6999
PSTN
Remote
FortiGate unit
in NAT mode
SIP Trunking SIP Trunking
LAN internal
172.20.120.10
wan1
192.168.10.10
external
192.168.40.10
SIP
a/b - wire
FortiGate Voice-80C
Internet
Note: You do not have to add SIP firewall policies to enable SIP traffic for the FortiGate
Voice unit to function as a PBX. Also, with PBX functionality enabled, you cannot apply
FortiGate SIP application control features to SIP traffic received by FortiGate Voice
interfaces for which you have enabled the SIP Traffic option.