Non-Proprietary Security Policy, Version 1.0 June 15, 2007
Polycom VSX 3000, VSX 5000, and VSX 7000s
Page 16 of 23
© 2007 Polycom, Inc. -
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
1.4 Roles and Services
The modules support two authorized roles (as required by FIPS 140-2) that operators may assume: a Crypto Officer
role and User role.
1.4.1 Crypto-Officer Role
The Crypto-Officer (CO) installs and uninstalls the cryptographic module. Also, the CO is responsible for
monitoring and configuring the modules and call settings.
The Crypto-Officer can manage the VSX modules over a Transport Layer Security (TLS) v1 session through a web
interface. Through this interface, the Crypto-Officer is able to configure the device and setup a call, change secure
mode of operation, monitor current status and perform virtually all of the management of the module. Configuration
of the modules and viewing of status can be performed with a Command Line Interface (CLI) over the local serial
port or remotely via Telnet over TLS. All the management and configuration capabilities are available via the
VSX’s web interface are also available via secure telnet over TLS. The telnet interface includes additional debug
commands that are not available over the web. The Crypto-Officer has access to the following services:
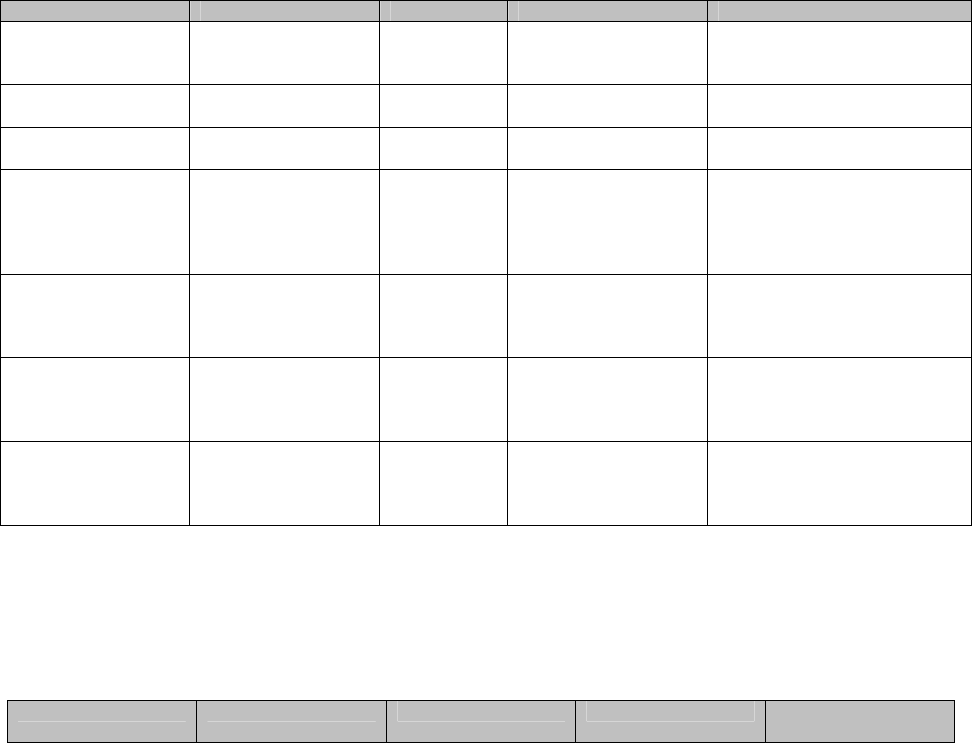
Table 7 - Mapping of Crypto-Officer’s Services to Inputs, Outputs, Critical Security Parameters (CSPs), and Access
Control
Service Description Input Output CSP and Access Control
Install Assemble the systems
and setup network
configurations
Command Result of installation None
Uninstall Disassemble the VSX
system
Command Uninstalled module None
Run Self-Test Perform the self-test
on demand
Command Status output None
Room monitoring Monitor meeting
rooms in or out of a
call using the Web
Director feature in
VSX Web.
Command Status output x.509 certificate – Read
Session key –Read/Write
CO password – Read
Remote diagnostics Identify and correct
issues that affect the
user’s experience via
VSX Web interface.
Command Status output x.509 certificate – Read
Session key –Read/Write
CO password – Read
Call Detail Reports Access the system’s
call history using local
or remote management
interface.
Command Modules’ settings and
status output
x.509 certificate – Read
Session key –Read/Write
CO password – Read
System configuration Run the system setup
wizard locally or
remotely to get the
system up and running.
Command Modules’ settings and
status output
x.509 certificate – Read
Session key –Read/Write
CO password – Read
1.4.2 User Role
Users access teleconferencing services via the LAN port (for IP calls) or the Network Interface Bay port (ISDN
calls). Services provided for Users are given below in Table 8.
Table 8 - Mapping of User’s Services to Inputs, Outputs, CSPs, and Access Control
Service Description Input Output CSP and Access
Control


















