Non-Proprietary Security Policy, Version 1.0 June 15, 2007
Polycom VSX 3000, VSX 5000, and VSX 7000s
Page 17 of 23
© 2007 Polycom, Inc. -
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
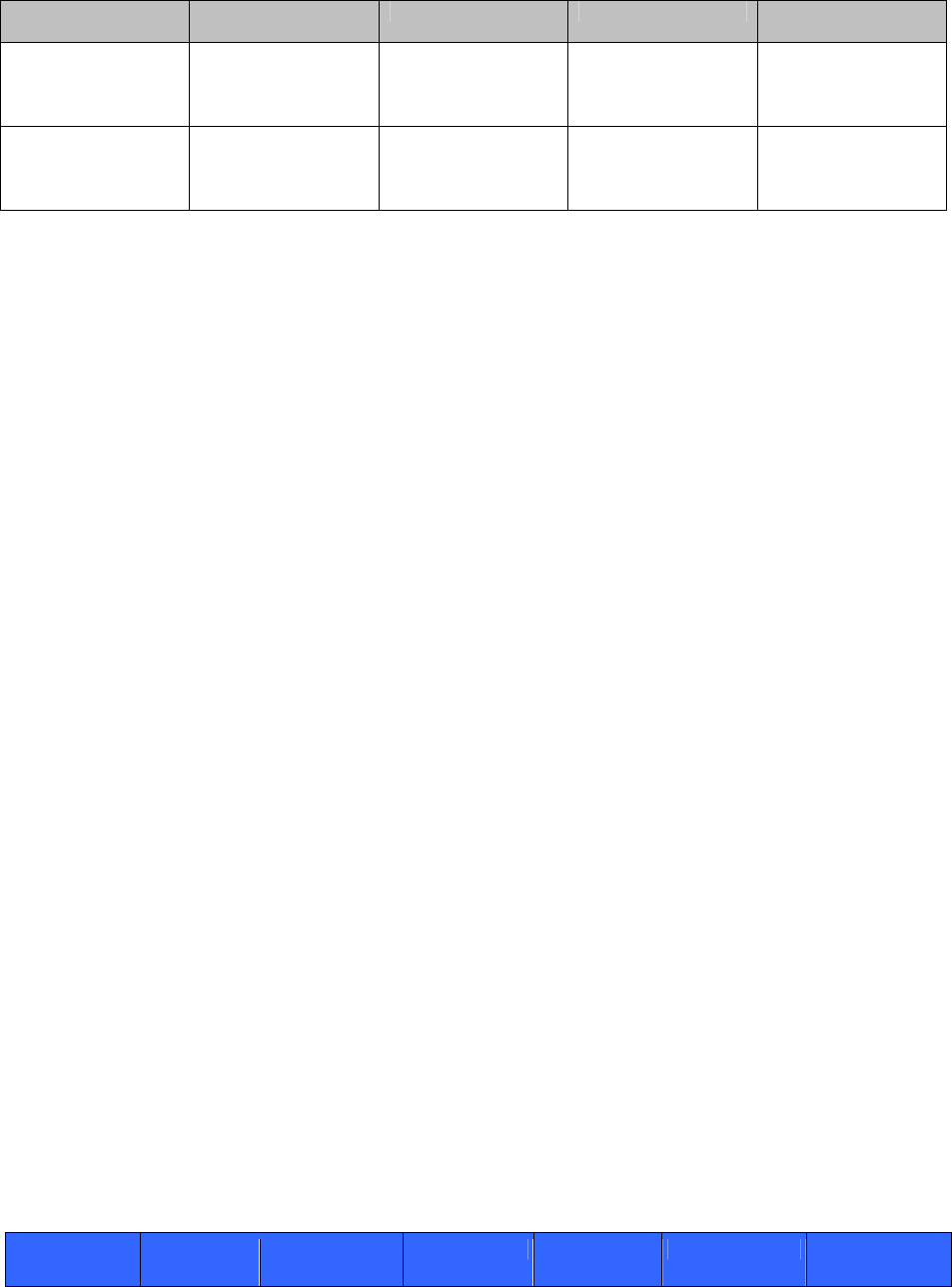
Service Description Input Output CSP and Access
Control
Secured call on IP
network
Placing secured call on
IP network via LAN
port
Command and calling
information
Connection established Diffie-Hellman key
pairs – Read
IP Encryption Key –
Read/Write
Secured call on ISDN Placing secured call on
ISDN via BRI/PRI
port
Command and calling
information
Connection established Diffie-Hellman key
pairs – Read
ISDN Encryption Key
– Read/Write
1.4.3 Authentication
The modules were not tested for role-based or identity-based authentication requirement as level 1 modules.
However, the modules authenticate Crypto-Officer with x.509 certificate during TLS handshake. The users do not
authenticate themselves to the module.
1.5 Physical Security
The VSX 3000, VSX 5000, and VSX 7000s are multi-chip standalone cryptographic modules. The modules’
hardware is composed of production-grade components and the modules are entirely enclosed in solid metal cases.
These cases enclose all of the modules’ internal components and serve as the cryptographic boundaries for the
modules.
The VSX systems were tested and found conformant to the Electromagnetic Interference/Electromagnetic
Compatibility (EMI/EMC) requirements specified by 47 Code of Federal Regulations, Part 15, Subpart B,
Unintentional Radiators, Digital Devices, Class A (i.e., for business use).
1.6 Operational Environment
The operational environment requirements do not apply to the VSX 3000, VSX 5000, and VSX 7000s. The modules
do not provide a general purpose Operating System (OS) and only allow the updating of image components after
checking a Digital Signature Algorithm (DSA) signature on new software images.
1.7 Cryptographic Key Management
The VSX modules implement the following FIPS-approved algorithms:
• AES (CBC, OFB) - key sizes 128, 192, 256 (Cert #431)
• FIPS 186-2 Appendix 3.1 PRNG (Cert #224)
• Secure Hashing Algorithm (SHA-1) – Byte oriented (Cert #501)
• TDES (CBC) 1, 2, 3 keying options (Cert #460)
• DSA (verify) 1024 bits (Cert #178)
Additionally, the module utilizes the following non-FIPS-approved algorithm implementation:
• Diffie-Hellman (key agreement, key establishment methodology provides 80-bits of encryption strength)
• RSA (key wrapping, key establishment methodology provides 80-bits of encryption strength)
• Hardware Random Number Generator (RNG) – for seeding the FIPS-approved deterministic RNG
The module supports the following critical security parameters:
Table 9 - List of Cryptographic Keys, Cryptographic Key Components, and CSPs
Key Key Type Generation /
Input
Output Storage Zeroization Use


















