Configuring EIGRP
EIGRP Configuration Task List
IPC-265
Cisco IOS IP Configuration Guide
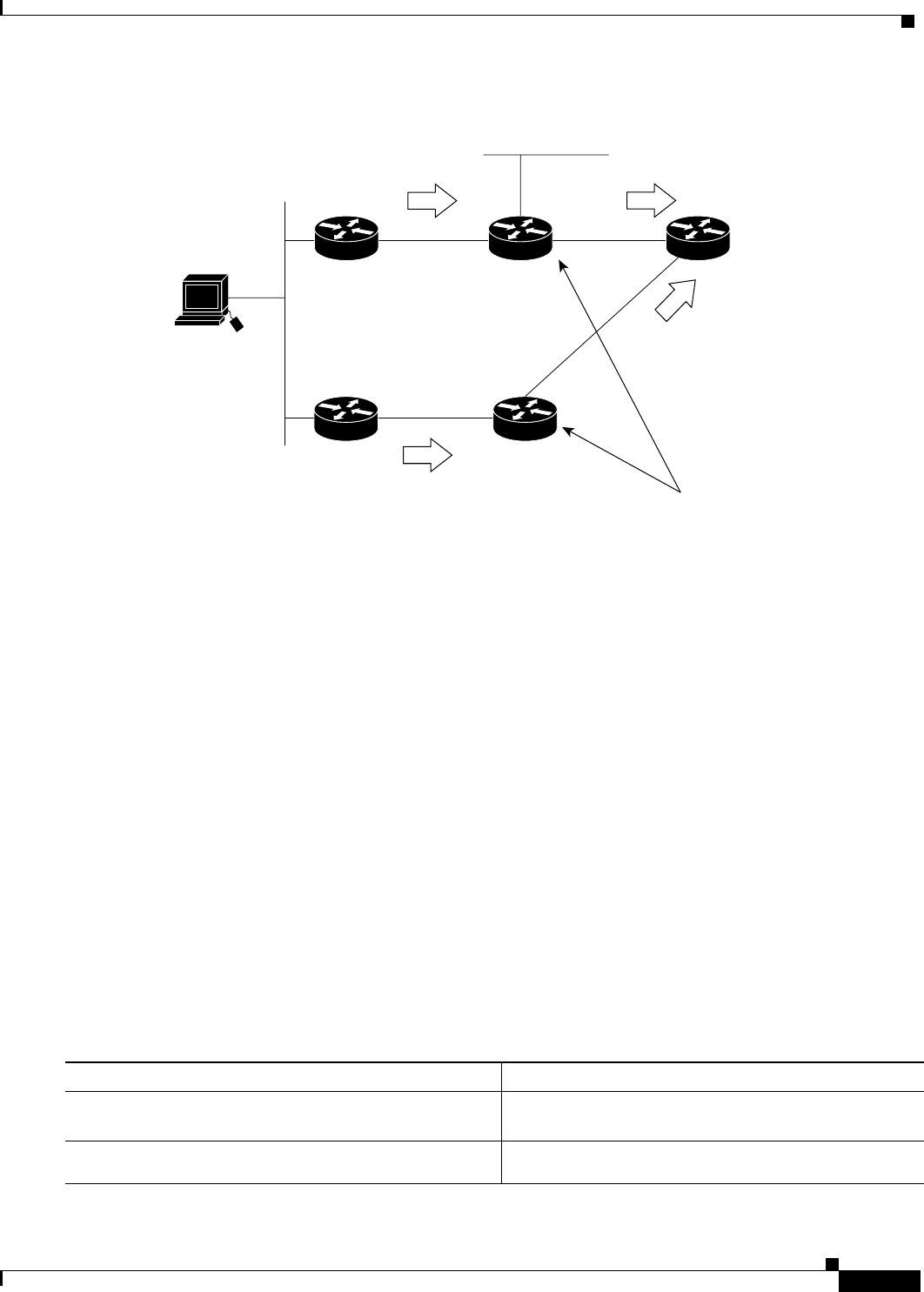
Figure 47 Floating Summary Route Applied for Dual-Homed Remotes
However, if the link between Router-D and Router-E fails, the network may blackhole traffic because
Router-E will continue to advertise the default route(0.0.0.0/0) to Router-C, as long as at least one link,
(other than the link to Router-C) to Router-E is still active. In this scenario, Router-C still forwards
traffic to Router-E, but Router-E drops the traffic creating the black hole. To avoid this problem, you
should configure the summary address with an administrative distance on only single-homed remote
routers or areas where there is only one exit point between to segments of the network. If two or more
exit points exist (from one segment of the network to another), configuring the floating default route can
cause a black hole to be formed.
Configuring EIGRP Route Authentication
EIGRP route authentication provides Message Digest 5 (MD5) authentication of routing updates from
the EIGRP routing protocol. The MD5 keyed digest in each EIGRP packet prevents the introduction of
unauthorized or false routing messages from unapproved sources.
Before you can enable EIGRP route authentication, you must enable EIGRP.
To enable authentication of EIGRP packets, use the following commands beginning in interface
configuration mode:
1
036
14
interface Serial 0/1
Router-B#show ip route
ip summary-address eigrp 100 0.0.0.0.0.0.0.0 250
. . . .
0.0.0.0.0.0.0.0 via <Router-A> (489765/170)
Router-D Router-E
Router-C
Router-A Router-B
0.0.0.0/0
0.0.0.0/0
0.0.0.0/0
0.0.0.0/0
10.1.1.0/24
Command Purpose
Step 1
Router(config)# interface type number
Configure an interface type and enter interface
configuration mode
Step 2
Router(config-if)# ip authentication mode eigrp
autonomous-system
md5
Enables MD5 authentication in EIGRP packets.


















